1,772 reads
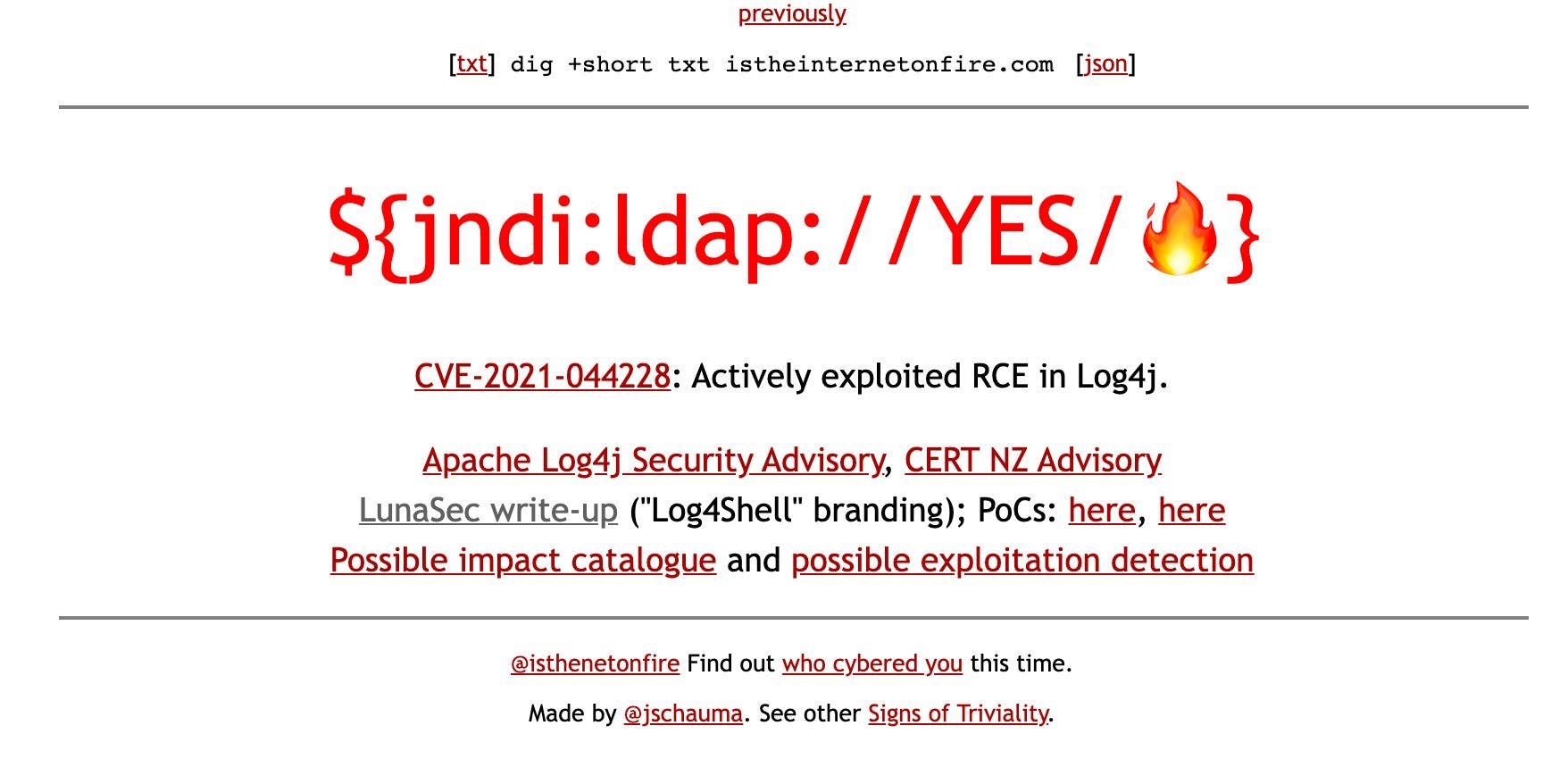
Log4J Vulnerability: A Legacy of Cybersecurity from Java to Blockchain and Minecraft
by
December 15th, 2021
Audio Presented by

Focused on the open source software supply chain to build a better digital future for all of us.
About Author
Focused on the open source software supply chain to build a better digital future for all of us.