380 reads
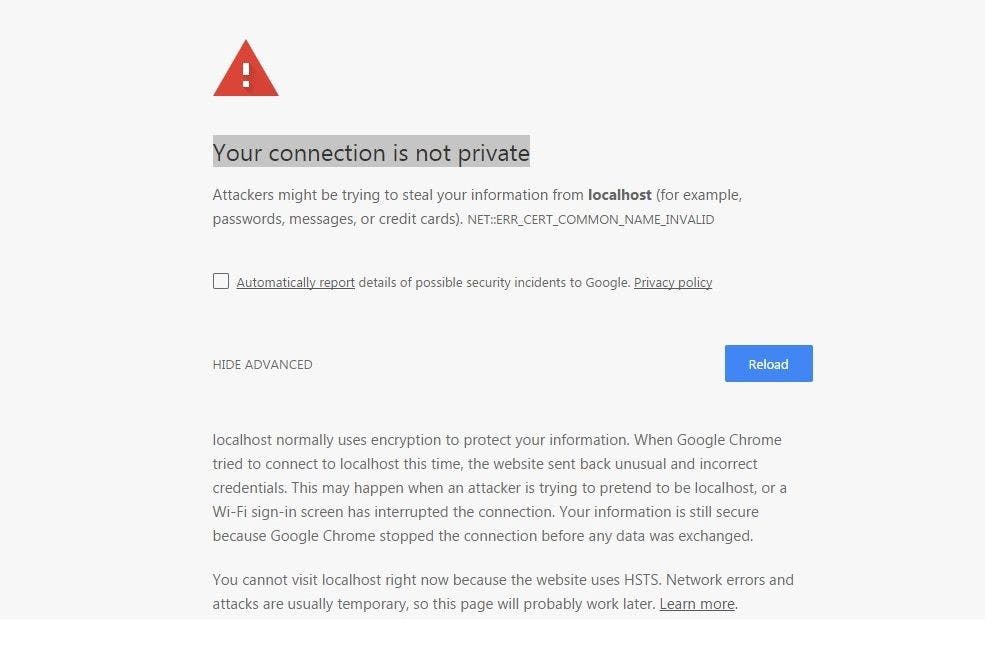
How Certificate Chains Works
by
June 12th, 2020

☁️ Cloud Software Consultant 🖊️ #DevOps 🚀 #Serverless ⚡#Javascript 🔥 #DotNet 👊 #MachineLearning
About Author
☁️ Cloud Software Consultant 🖊️ #DevOps 🚀 #Serverless ⚡#Javascript 🔥 #DotNet 👊 #MachineLearning